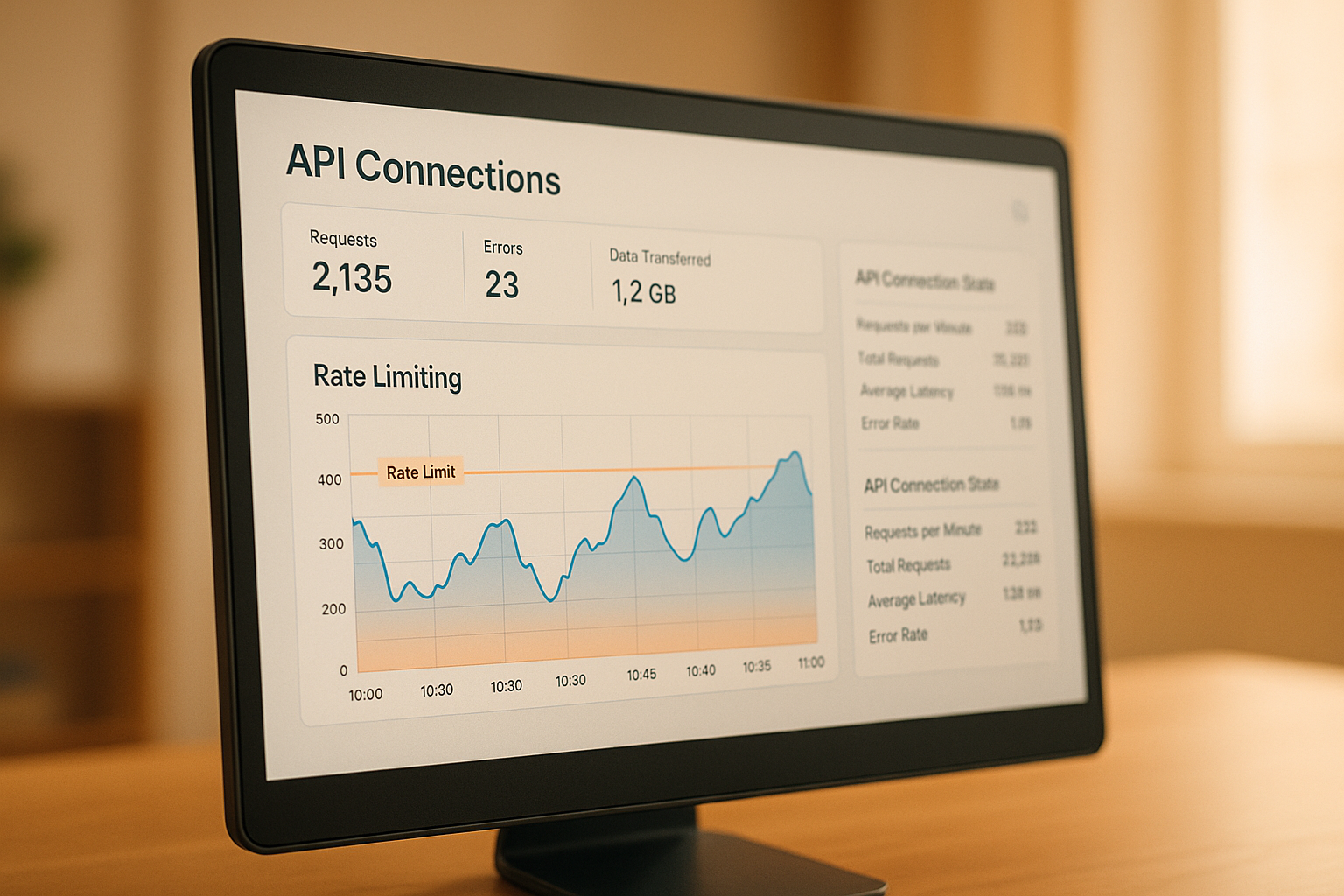
Rate limiting is a critical tool for managing API traffic, ensuring systems remain stable and resources are fairly distributed. It involves setting thresholds for API requests over a specific time frame to protect against overuse, abuse, or unexpected traffic spikes. Here's what you need to know:
Key Benefits of Rate Limiting:
- Protects Resources: Prevents system overload by capping traffic.
- Ensures Fair Access: Balances usage among users and applications.
- Controls Costs: Avoids unexpected expenses from traffic surges.
Common Use Cases:
- Mitigating DDoS attacks.
- Enforcing service-level agreements (SLAs).
- Managing partner API traffic.
- Maintaining system reliability in microservices.
Steps to Implement Rate Limiting:
- Define Goals: Set limits based on system capacity, user tiers, and cost considerations.
- Analyze Traffic: Use historical data to identify patterns and peak usage.
- Choose an Algorithm: Options include Token Bucket, Leaky Bucket, Fixed Window Counter, Sliding Window Log, and Sliding Window Counter.
- Set Limits: Configure API gateways or middleware to enforce limits by user, IP, or endpoint.
- Handle Responses: Use HTTP 429 status codes with headers like
X-RateLimit-LimitandRetry-Afterfor transparency. - Monitor and Adjust: Track metrics, detect anomalies, and adapt limits based on system load.
Algorithm Overview:
- Token Bucket: Handles bursts effectively.
- Leaky Bucket: Maintains steady traffic flow.
- Fixed Window Counter: Simple but prone to timing exploits.
- Sliding Window Log: Highly precise but memory-intensive.
- Sliding Window Counter: Balances accuracy and efficiency for high-traffic systems.
Implementation Tips:
- Use API gateways (e.g., AWS, Azure, Kong) for easy setup.
- Ensure clear communication with developers through headers, error messages, and documentation.
- Regularly review and refine policies based on system performance and business needs.
Takeaway: Rate limiting is essential for system stability, security, and cost management. By choosing the right strategy and tools, you can safeguard your APIs while ensuring a smooth user experience.
Rate Limiting system design | TOKEN BUCKET, Leaky Bucket, Sliding Logs
Planning Your Rate Limiting Strategy
Creating an effective rate limiting strategy is all about finding the right balance. You need to protect your infrastructure while ensuring that legitimate users can still access your services without unnecessary frustration. This requires clear goals and a methodical approach to traffic management.
Set Clear Goals and Service Tiers
Before diving into implementation, it’s essential to define what you want to achieve. Your priorities will shape your strategy, and these can vary widely depending on your business needs.
Start by focusing on infrastructure protection. For instance, if your API typically handles 10,000 requests per minute during peak times, you might set a safeguard limit of 15,000 requests per minute. This ensures your system can handle unexpected surges without compromising stability.
Fair usage enforcement is another key consideration, especially if you cater to different types of clients. For example, internal applications, premium partners, and free-tier users might all have different access needs. Your strategy should ensure that high-priority clients get consistent access while preventing any single user from hogging resources.
Don’t overlook cost management. In cloud environments, every API call can translate to a direct expense. Setting well-thought-out limits helps you control costs and avoid surprises from unexpected traffic spikes.
To manage these priorities effectively, define clear service tiers. Each tier should reflect the needs of your users and include specific limits, reset periods, and escalation paths. For instance:
- A premium tier might allow up to 1,000 requests per minute with a burst capacity of 1,500.
- A standard tier could limit users to 100 requests per minute with no burst option.
Once you’ve mapped out your goals and tiers, take a close look at your traffic data to ensure your limits are realistic.
Analyze Traffic Patterns and System Capacity
Understanding how your system handles traffic is the cornerstone of a successful rate limiting strategy. Without this insight, you’re essentially guessing - and that can lead to either system instability or unhappy users.
Start by reviewing historical traffic data. Identify trends, such as peak usage periods, and set limits that can adapt to these patterns. For example, if your API usually processes 500 requests per minute but spikes to 2,000 during monthly report generation, your limits should account for these legitimate surges while still blocking malicious traffic.
Endpoint-specific analysis is also critical. Not all API endpoints are created equal - some are lightweight, like user authentication, while others, like data aggregation, might demand significant system resources. Tailor your limits accordingly to ensure stability without penalizing efficient operations.
Consider implementing adaptive limits that adjust based on system capacity. For example, during high server load, you could temporarily lower rate limits to maintain stability, then restore normal limits once the load decreases. This approach requires real-time monitoring of key metrics like CPU usage, memory, and database connections.
With a clear understanding of your traffic and system capabilities, you can configure the scope and parameters of your rate limiting rules.
Configure Rate Limit Scope and Parameters
Choosing the right scope for your rate limits is crucial. Different scoping methods address different challenges, and many organizations use a combination of approaches.
Here are some common scoping strategies:
- API key-based limits: Manage access on a per-client basis.
- User-based limits: Prevent individual users from overloading your system.
- IP-based restrictions: Block abusive behavior at the network level.
- Endpoint-specific quotas: Protect resource-heavy operations.
- Tenant-based allocation: In multi-tenant setups, ensure each customer gets a fair share of resources.
For multi-tenant environments, tenant-based limits are especially important. Allocate quotas to each tenant to prevent one customer’s usage from affecting others. This requires careful tracking of tenant relationships and their associated resource usage.
When configuring rate limits, you’ll also need to decide on time windows and burst allowances. A sliding window approach offers smoother rate limiting compared to fixed intervals, though it’s more complex to implement. Burst allowances, on the other hand, let users temporarily exceed their limits - for example, allowing 150 requests in one minute as long as the five-minute average stays below 100 requests per minute.
Finally, choose between fixed interval resets and sliding windows based on your system’s needs. Fixed intervals are simpler to manage and explain, while sliding windows provide a more user-friendly experience by smoothing out traffic spikes.
Choose the Right Rate Limiting Algorithm
Selecting the right rate limiting algorithm is crucial for balancing your API's ability to handle traffic bursts, ensure consistent performance, and protect against abuse. Your decision will directly affect how your system manages spikes in traffic, accommodates legitimate surges, and enforces limits effectively.
Rate Limiting Algorithm Comparison
When it comes to rate limiting, there are five commonly used algorithms, each with its own strengths and weaknesses. Here's a quick breakdown:
- Token Bucket: This algorithm allows bursts by consuming tokens from a bucket. It's great for handling intermittent traffic surges but requires careful tuning of the bucket size and refill rate. However, it doesn't promise perfectly smooth traffic rates.
- Leaky Bucket: Think of a bucket with a small hole at the bottom - it ensures a steady flow by smoothing out bursts. While it provides fairness, it may stumble with short-lived spikes and introduces extra computational overhead to manage the queue.
- Fixed Window Counter: This approach divides time into fixed intervals and counts requests within each window. It's simple to implement and works well for steady traffic. However, users can exploit boundary timing to send more requests than allowed.
- Sliding Window Log: This algorithm offers high precision by logging each request, but its memory requirements make it less suitable for high-traffic environments.
- Sliding Window Counter: A hybrid of fixed and sliding windows, this algorithm uses overlapping counters for better accuracy. It’s efficient for high-traffic scenarios, as demonstrated by Cloudflare, which found only a 0.003% error rate across 400 million requests.
| Algorithm | Memory Usage | Complexity | Burst Handling | Precision | Best For |
|---|---|---|---|---|---|
| Token Bucket | Efficient | Moderate | Excellent | Good | Handling bursts |
| Leaky Bucket | Moderate | Moderate | Poor | Excellent | Consistent traffic rates |
| Fixed Window Counter | Very Low | Simple | Poor | Fair | Simple use cases |
| Sliding Window Log | High | Complex | Good | Excellent | Precision for low traffic |
| Sliding Window Counter | Moderate | Complex | Good | Excellent | High-traffic accuracy |
The right algorithm can help manage traffic effectively while safeguarding your API from misuse. Use this comparison to identify the best fit for your needs.
Match Algorithms to Your Use Case
Your API’s usage patterns and service level agreements (SLAs) should guide your choice of algorithm.
- For bursty traffic, the Token Bucket is a solid choice. For instance, if your API supports mobile apps or user-generated content uploads, users often generate bursts of activity. Token Bucket absorbs these bursts while preventing prolonged abuse.
- For systems needing consistency, like financial platforms or real-time monitoring tools, the Leaky Bucket ensures smooth, predictable traffic flow. It’s ideal when steady performance is non-negotiable.
- For high-volume APIs, such as public-facing APIs handling millions of requests per hour, the Sliding Window Counter offers excellent accuracy without the heavy memory demands of request logs.
- For simple internal APIs or prototypes, Fixed Window Counter is a good starting point. While it has its limitations, its simplicity makes it easy to implement and refine as your needs grow.
SLAs also play a key role. For example, if your SLA promises users 1,000 requests per minute with occasional bursts up to 1,500, the Token Bucket naturally aligns with this requirement. On the other hand, if you guarantee consistent processing times, the Leaky Bucket may be a better fit.
Implementation Considerations and Trade-offs
Once you’ve chosen an algorithm, it’s essential to address potential challenges during implementation. Here are some key factors to keep in mind:
- Race conditions: In distributed systems, concurrent requests can cause inconsistencies in counter updates. Algorithms like Token Bucket and Leaky Bucket are particularly vulnerable. To maintain accuracy, use synchronization mechanisms like distributed locks or atomic operations.
- Computational overhead: More complex algorithms, such as Sliding Window Counter, require additional processing power to manage multiple counters. While this overhead may seem negligible for individual requests, it can add up quickly under heavy traffic.
- Accuracy needs: If your business model relies on precise rate limiting - such as tiered API pricing - accuracy is critical. For example, the Sliding Window Counter’s 0.003% error rate may be acceptable, but Fixed Window Counter’s boundary issues could lead to disputes.
- Scalability: Simpler algorithms like Fixed Window Counter scale easily with user growth, whereas more complex algorithms may require additional infrastructure to maintain performance. Plan ahead to ensure your system can handle future demand.
Implement Rate Limiting Policies
Once you've chosen your rate limiting algorithm, it's time to put it into action by setting up policies and managing responses. This step is critical for safeguarding your API while ensuring a smooth experience for developers using it.
Configure Limits Using API Gateways and Middleware
API gateways like AWS API Gateway, Azure API Management, or Kong offer built-in rate limiting tools that let you enforce limits without altering your application code. You can define policies that control rate limits by API key, IP address, or user tier. For example, you might allow 1,000 requests per hour for basic users and 10,000 requests per hour for premium users. These policies can be applied globally, to specific API routes, or even to individual HTTP methods.
If you need more flexibility, custom middleware is a great option. Middleware intercepts requests before they reach your app's core logic. It checks whether a request exceeds the limit and either lets it pass or blocks it with an appropriate response. For instance, your API gateway might enforce a broad limit of 5,000 requests per hour, while your middleware adds more nuanced restrictions, such as limiting resource-heavy operations.
In distributed systems, shared caches like Redis or database-backed counters can help maintain a consistent state across multiple servers.
The next step is ensuring your API communicates clearly when limits are exceeded.
Handle Rate Limit Exceeded Responses
When a client hits their limit, your API should respond with an HTTP status code 429 (Too Many Requests). This code immediately signals that rate limiting is in effect.
Include response headers to help clients adjust their behavior. For example:
- X-RateLimit-Limit: Maximum requests allowed in the current window.
- X-RateLimit-Remaining: Requests left before hitting the limit.
- X-RateLimit-Reset: When the limit will reset, often as a Unix timestamp or seconds remaining.
Here’s an example of a well-structured 429 response:
HTTP/1.1 429 Too Many Requests
X-RateLimit-Limit: 1000
X-RateLimit-Remaining: 0
X-RateLimit-Reset: 1640995200
Retry-After: 3600
Content-Type: application/json
{
"error": "Rate limit exceeded",
"message": "You have exceeded your hourly limit of 1000 requests. Please try again in 1 hour.",
"retry_after": 3600
}
The Retry-After header is particularly helpful, as it tells clients when they can retry. This value can be provided in seconds (e.g., "3600" for one hour) or as an HTTP date. Well-designed clients will respect this header and retry only after the specified time.
For a better user experience, consider graceful degradation. Instead of outright blocking users nearing their limits, you could reduce functionality. For instance, you might disable real-time features but still allow basic API operations. This approach encourages users to upgrade their plan rather than feeling completely shut out.
Provide Clear Error Messages and User Feedback
When rate limits are exceeded, error messages should be specific and actionable. Vague responses like "Request denied" frustrate developers and lead to unnecessary support inquiries. Instead, explain why the request was blocked and what the client can do next. For example:
"You have exceeded your daily limit of 50,000 requests. Your limit will reset at midnight UTC (in 8 hours and 23 minutes)."
To prevent violations, you can also send proactive notifications. For instance, include headers like X-RateLimit-Warning in successful responses when a client is nearing their limit (e.g., 80% or 90% usage). This gives them time to adjust their request patterns.
Detailed documentation is another must-have. Your API documentation should outline all rate limiting policies, including limits for specific endpoints and user tiers. Include examples of how to handle 429 responses and respect Retry-After headers in popular programming languages.
Developer dashboards can further enhance transparency. By showing real-time and historical usage data - like current quota, remaining requests, and usage trends - developers can optimize their integrations to avoid hitting limits. This self-service approach not only improves their experience but also reduces the load on your support team.
Lastly, tailor error messages to different audiences. Machine-to-machine integrations benefit from structured JSON responses with consistent field names, while human-facing apps might need friendlier, more conversational messages that are easy for end users to understand.
sbb-itb-91124b2
Monitor and Scale Rate Limiting Systems
Setting up rate limiting is just the beginning. To keep your API running smoothly as traffic patterns shift, it's crucial to monitor and adjust your system regularly. Without proper oversight, even the best-designed limits can become obstacles or fail to address new threats effectively.
Track API Usage and Spot Unusual Activity
The foundation of good monitoring is thorough analytics that capture both typical usage patterns and anything out of the ordinary. Use monitoring tools to keep an eye on essential metrics like request volumes, response times, and rate limit violations.
Set up dashboards to track real-time and historical data. Focus on metrics such as requests per minute, unique IP addresses, and the percentage of requests hitting rate limits. For larger systems, analyze these metrics by API endpoint, user tier, region, or time of day for a more detailed view.
Anomaly detection tools can help identify suspicious activity or system issues. For instance, if your API normally handles 50,000 requests per hour during business hours but suddenly gets 200,000 requests from one IP range, your system should flag it. Similarly, if premium users who rarely hit their limits suddenly max out, it could signal a security issue or a problem with their integration.
Automated alerts should notify your team of unusual patterns, providing context such as affected endpoints, user groups, and potential system impacts.
Log analysis adds another layer of insight. By parsing API logs, you can uncover trends like which endpoints are frequently rate-limited, which time zones drive the most traffic, or whether specific user agents or IP ranges show suspicious behavior. This data can guide adjustments to your rate limiting strategy and help you fine-tune system performance.
Adapt Limits Based on System Load
Real-time analytics allow you to tweak your API limits as system demands change. While static rate limits are a good starting point, dynamic adjustments can help manage fluctuating loads. Monitor system resources like CPU usage, memory, and database connections alongside rate limiting metrics.
Load-based rate limiting lets you adapt to stress on your system. For example, if your database CPU usage hits 80%, you might temporarily lower API limits by 20% to prevent a system crash. On the flip side, during low-traffic periods, you could increase limits to enhance the user experience.
Use circuit breaker patterns to manage dependencies. If a service your API relies on is struggling, temporarily reduce limits for endpoints that depend on it. This protects both your API and the affected service.
Seasonal traffic patterns should also guide your planning. For example, if you support e-commerce platforms, expect traffic surges during holiday seasons. Gradually increase limits ahead of these spikes and have rollback plans ready in case issues arise.
A/B testing can help refine your rate limiting policies. Experiment with different configurations on small user groups to see how changes affect both performance and user satisfaction. For example, you might test increasing limits for premium users by 25% to gauge whether it improves their experience without straining your system.
Ensure Governance and Compliance
To maintain stability and meet regulatory requirements, rate limiting needs a strong governance framework. Use version-controlled policies (e.g., with Open Policy Agent) to track and manage changes consistently across development, staging, and production environments.
Audit trails are critical for both compliance and troubleshooting. Log all policy changes, including who made them, when, and why. Also, track rate limiting decisions at the request level, noting which rules were applied and whether requests were allowed or blocked. This data is invaluable during security reviews or compliance audits.
Schedule regular policy reviews - quarterly, for example - to ensure your limits align with system capabilities and business goals. Involve stakeholders from security, operations, and business teams to balance technical needs with broader objectives.
If your API handles sensitive data, compliance monitoring is non-negotiable. For example, financial APIs might need to prove that their rate limits prevent abuse while still allowing legitimate access. Document your policies and show evidence of regular reviews and updates based on real-world usage and emerging threats.
Finally, implement change management processes for updating rate limits. Require security and operations approval for major changes, and roll out updates gradually to avoid disruptions. This ensures that your policies are both effective and carefully implemented.
Testing and Deployment Checklist
Thorough testing and a careful deployment process are critical to avoiding costly errors and service interruptions.
Test Rate Limits Before Production
Load testing is essential to ensure your rate limiting behaves as expected under real-world conditions. Tools like Apache JMeter or k6 can simulate production-level traffic. For example, test different user tiers - such as basic users capped at 1,000 requests per minute (rpm) and premium users at 5,000 rpm - to confirm limits are correctly enforced for each group.
Spike testing evaluates how your system handles sudden surges in traffic. Simulate scenarios where traffic jumps to 10 times the normal load within 30 seconds and sustains for 5 minutes. Watch for issues like memory leaks, connection exhaustion, or cascading failures. Your rate limiting should handle these spikes smoothly without causing system crashes.
Don’t overlook edge cases that might not occur during regular operations. Test scenarios like users sending exactly the maximum allowed requests per second or multiple users from the same IP hitting their limits simultaneously. Also, examine how your system behaves during database slowdowns or when external services are unavailable.
Validation testing ensures your rules function as intended. For instance, test whether exceeding a 10,000 rpm limit triggers the correct error response after the 10,001st request. Check time window boundaries by sending requests right before and after reset periods to confirm counters reset as expected.
Implement synthetic monitoring to continuously test rate limiting behavior. Set up automated checks every 15 minutes to send requests at varying rates. This proactive approach helps identify configuration issues or system errors before they affect users.
Successful testing ensures your system is ready for a controlled and monitored deployment phase.
Deploy with Monitoring and Observability
Once pre-production testing is complete, move to deployment with robust monitoring and observability in place.
Canary deployments allow you to roll out changes incrementally. Start by routing 5% of traffic through the new configuration, then gradually increase to 25%, 50%, and finally 100% over several hours or days. Closely monitor error rates, response times, and user feedback at each stage.
Set up real-time dashboards to track critical metrics during deployment. Monitor requests per second, rate limit violations, error rates, and resource usage. Configure alerts to notify your team if error rates exceed 0.5% or if rate limit violations spike unexpectedly. This enables quick detection and resolution of issues.
Use detailed logging to capture valuable troubleshooting data. Log every rate limiting decision, including user ID, IP address, endpoint, current usage, and limit thresholds. Include timing details to pinpoint performance bottlenecks. Structured JSON logs make it easier to analyze the data later.
Prepare rollback procedures before deployment starts. Define clear rollback criteria, such as error rates exceeding 1% or a surge in customer complaints. Ensure your team can revert to the previous configuration within 5 minutes. Test rollback plans in staging to avoid confusion during live incidents.
Consider blue-green deployments for major changes. Run the new configuration alongside the existing one and gradually shift traffic between them. This approach allows you to compare performance metrics and switch back instantly if issues arise.
Update Documentation and Developer Resources
After deployment, update your documentation and developer tools to reflect the latest rate limiting implementation.
Your developer portal documentation should clearly outline rate limits (e.g., "Basic users: 1,000 rpm; Premium users: 10,000 rpm"). Include code examples for handling 429 responses and implementing retry logic with exponential backoff. Avoid vague descriptions - be specific and provide actionable guidance.
Expand your error response documentation to help developers handle rate limiting effectively. Detail the HTTP status codes, headers, and response bodies your API returns when limits are exceeded. Explain how to use the Retry-After header and include examples for both JSON and XML formats if supported.
Develop best practices guides to help developers optimize their usage. Share techniques like batching requests, caching responses, and using webhooks instead of polling. Provide sample code in popular programming languages to demonstrate proper rate limiting handling.
Use change notifications to keep developers informed about updates. Announce changes through your developer newsletter, API status page, and in-app notifications. Give at least 30 days' notice for any limit reductions, along with clear explanations and migration guides for new features.
Add interactive examples to your documentation to let developers safely test rate limiting behavior. Offer a sandbox environment where they can experiment with different request patterns and observe the system’s responses. Include simulators to demonstrate what happens as limits are approached or exceeded.
Key Takeaways for Enterprise Rate Limiting
Effective rate limiting is all about making informed decisions and refining your approach over time. Start by grounding your limits in real data. Analyze historical traffic to understand peak loads, typical user behavior, and your system's capacity. This ensures you're setting thresholds that balance protection for your systems without frustrating legitimate users.
Choosing the right algorithm is critical. Different traffic patterns call for different solutions. For instance, the token bucket algorithm is ideal for handling bursty traffic, such as requests from mobile apps or IoT devices. On the other hand, fixed window algorithms work well for predictable operations like CRUD tasks. If you're dealing with high-stakes scenarios, such as financial transactions, sliding window algorithms provide the precision you need, though they may require more memory. Tailor your algorithm choices to each endpoint based on its unique usage patterns.
When designing rate limits, think beyond technical constraints - align them with the business value of your API. A tiered approach that reflects how your API contributes to your business can be a strong strategy. For U.S.-based enterprises, this often means creating service levels with specific burst allowances and negotiated SLAs. Reviewing these limits regularly, using metrics like latency percentiles and error rates, will help you stay aligned with both technical and business goals.
Communication is non-negotiable. When users hit rate limits, provide actionable feedback. Include headers like X-RateLimit-Remaining to show how close they are to their limit and Retry-After with ISO 8601 timestamps to guide them on when they can try again. Real-time quota visibility through developer portals can also empower teams to self-manage their usage.
Great implementations rely on robust monitoring and adaptability. Keep an eye on metrics like requests per second, 429 error rates, and outliers per key. Monitor how these correlate with downstream service performance. Automate adjustments for predictable traffic spikes, but ensure you have rollback procedures in place for smooth recovery when needed.
For more complex needs, consider advanced enterprise strategies. Techniques like rate limit partitioning, request coalescing, intelligent caching, and circuit breakers can provide an extra layer of protection for your services.
Centralized enforcement through API gateways simplifies governance and ensures consistency. With this approach, you can enforce policies at a high level - such as per-key or per-route rules - while still allowing for middleware to handle endpoint-specific requirements. This also provides consistent audit trails, which are essential for compliance in enterprise environments.
For enterprises using platforms like Sitecore or Adobe Experience Manager, integrating rate limits across multiple APIs and channels can be a challenge. In these cases, working with experts like Kogifi can help you align rate limiting with your broader omnichannel strategy. This ensures consistent performance and adherence to SLAs across your entire tech stack.
Lastly, rate limiting is not a set-it-and-forget-it task. Regular reviews with your SRE and product teams are essential. These reviews help you spot abuse patterns, assess capacity needs, and adjust to evolving business requirements. The ultimate goal is to strike a balance between protecting your systems and delivering a great user experience - something that will naturally evolve as your enterprise grows.
FAQs
How can I effectively communicate API rate limit policies to developers and users to ensure clarity and compliance?
To maintain clarity and compliance, it's crucial to communicate API rate limit policies in a straightforward way. Start by creating detailed documentation that outlines the rate limits, explains how they function, and describes the consequences of exceeding them. This ensures developers have a clear understanding from the outset.
In addition to documentation, use response headers and status codes to give developers real-time updates on their usage. These tools can alert them when they're approaching or surpassing the set limits, helping them adjust accordingly.
It's also important to keep users in the loop by sending advance notifications about any updates to the rate limit policies. This approach builds trust and reduces the chance of unexpected disruptions. Clear and consistent communication allows developers to manage their usage effectively while ensuring a smooth and positive experience.
How can enterprises implement rate limiting without negatively impacting the user experience?
To ensure effective rate limiting without compromising the user experience, businesses can implement adaptive rate limiting. This method dynamically adjusts request limits based on real-time factors like user activity, system performance, and traffic levels. By aligning limits with actual usage patterns, you can avoid unnecessary restrictions while keeping your system stable.
Other useful techniques include incorporating burst capacity to handle temporary traffic spikes, applying dynamic throttling to scale limits during periods of high demand, and providing clear communication about rate limits in API documentation or error messages. These approaches not only protect your infrastructure from overload but also help maintain a seamless experience for users.
What challenges can arise when using different rate limiting algorithms, and how can they be resolved?
Managing rate limiting algorithms comes with its own set of challenges, including increased resource consumption, handling unexpected traffic surges, and added complexity in system design. While algorithms like the token bucket or leaky bucket are great for regulating and smoothing traffic, they can demand a lot of processing power, especially during peak usage. Sudden spikes in traffic can also overwhelm the system or inadvertently block legitimate requests.
To tackle these challenges, you might want to explore adaptive algorithms that can dynamically adjust limits based on real-time traffic behavior. Another effective approach is using distributed rate limiters, which can scale efficiently to meet the demands of high-traffic environments. These methods can help maintain consistent performance and reliability, particularly for enterprise-level APIs.